Applies to
- Windows 10
This topic provides a high-level overview of BitLocker, including a list of system requirements, practical applications, and deprecated features.
Bitlocker, BitLocker Drive Encryption, EFS, Encrypting File System, gpedit.msc, Group Policy Editor, TPM, Trusted Platform Module, Windows 10 BitLocker Videos You May Like Windows 10 Features and Navigation – December 1, 2015. BitLocker used to require an Enterprise or Ultimate copy of Windows 7. These days, it is included with Windows 10 Pro, which many people get OEM with their computer. This is great news, because it means that you will be able to fully encrypt your hard drive, making it much safer in the event of loss or theft.
BitLocker overview
BitLocker Drive Encryption is a data protection feature that integrates with the operating system and addresses the threats of data theft or exposure from lost, stolen, or inappropriately decommissioned computers.
BitLocker provides the most protection when used with a Trusted Platform Module (TPM) version 1.2 or later. The TPM is a hardware component installed in many newer computers by the computer manufacturers. It works with BitLocker to help protect user data and to ensure that a computer has not been tampered with while the system was offline.
On computers that do not have a TPM version 1.2 or later, you can still use BitLocker to encrypt the Windows operating system drive. However, this implementation will require the user to insert a USB startup key to start the computer or resume from hibernation. Starting with Windows 8, you can use an operating system volume password to protect the operating system volume on a computer without TPM. Both options do not provide the pre-startup system integrity verification offered by BitLocker with a TPM.
In addition to the TPM, BitLocker offers the option to lock the normal startup process until the user supplies a personal identification number (PIN) or inserts a removable device, such as a USB flash drive, that contains a startup key. These additional security measures provide multifactor authentication and assurance that the computer will not start or resume from hibernation until the correct PIN or startup key is presented.
Practical applications
Data on a lost or stolen computer is vulnerable to unauthorized access, either by running a software-attack tool against it or by transferring the computer's hard disk to a different computer. BitLocker helps mitigate unauthorized data access by enhancing file and system protections. BitLocker also helps render data inaccessible when BitLocker-protected computers are decommissioned or recycled.
There are two additional tools in the Remote Server Administration Tools, which you can use to manage BitLocker.
BitLocker Recovery Password Viewer. The BitLocker Recovery Password Viewer enables you to locate and view BitLocker Drive Encryption recovery passwords that have been backed up to Active Directory Domain Services (AD DS). You can use this tool to help recover data that is stored on a drive that has been encrypted by using BitLocker. The BitLocker Recovery Password Viewer tool is an extension for the Active Directory Users and Computers Microsoft Management Console (MMC) snap-in.By using this tool, you can examine a computer object's Properties dialog box to view the corresponding BitLocker recovery passwords. Additionally, you can right-click a domain container and then search for a BitLocker recovery password across all the domains in the Active Directory forest. To view recovery passwords, you must be a domain administrator, or you must have been delegated permissions by a domain administrator.
BitLocker Drive Encryption Tools. BitLocker Drive Encryption Tools include the command-line tools, manage-bde and repair-bde, and the BitLocker cmdlets for Windows PowerShell. Both manage-bde and the BitLocker cmdlets can be used to perform any task that can be accomplished through theBitLocker control panel, and they are appropriate to use for automated deployments and other scripting scenarios. Repair-bde is provided for disaster recovery scenarios in which a BitLocker protected drive cannot be unlocked normally or by using the recovery console.
New and changed functionality
To find out what's new in BitLocker for Windows 10, such as support for the XTS-AES encryption algorithm, see the BitLocker section in 'What's new in Windows 10.'
System requirements
BitLocker has the following hardware requirements:
For BitLocker to use the system integrity check provided by a Trusted Platform Module (TPM), the computer must have TPM 1.2 or later. If your computer does not have a TPM, enabling BitLocker requires that you save a startup key on a removable device, such as a USB flash drive.
A computer with a TPM must also have a Trusted Computing Group (TCG)-compliant BIOS or UEFI firmware. The BIOS or UEFI firmware establishes a chain of trust for the pre-operating system startup, and it must include support for TCG-specified Static Root of Trust Measurement. A computer without a TPM does not require TCG-compliant firmware.
The system BIOS or UEFI firmware (for TPM and non-TPM computers) must support the USB mass storage device class, including reading small files on a USB flash drive in the pre-operating system environment.
Note
TPM 2.0 is not supported in Legacy and CSM Modes of the BIOS. Devices with TPM 2.0 must have their BIOS mode configured as Native UEFI only. The Legacy and Compatibility Support Module (CSM) options must be disabled. For added security Enable the Secure Boot feature.
Installed Operating System on hardware in legacy mode will stop the OS from booting when the BIOS mode is changed to UEFI. Use the tool MBR2GPT before changing the BIOS mode which will prepare the OS and the disk to support UEFI.
The hard disk must be partitioned with at least two drives:
- The operating system drive (or boot drive) contains the operating system and its support files. It must be formatted with the NTFS file system.
- The system drive contains the files that are needed to load Windows after the firmware has prepared the system hardware. BitLocker is not enabled on this drive. For BitLocker to work, the system drive must not be encrypted, must differ from the operating system drive, and must be formatted with the FAT32 file system on computers that use UEFI-based firmware or with the NTFS file system on computers that use BIOS firmware. We recommend that system drive be approximately 350 MB in size. After BitLocker is turned on it should have approximately 250 MB of free space.
When installed on a new computer, Windows will automatically create the partitions that are required for BitLocker.
When installing the BitLocker optional component on a server you will also need to install the Enhanced Storage feature, which is used to support hardware encrypted drives.
In this section
| Topic | Description |
|---|---|
| Overview of BitLocker Device Encryption in Windows 10 | This topic for the IT professional provides an overview of the ways that BitLocker Device Encryption can help protect data on devices running Windows 10. |
| BitLocker frequently asked questions (FAQ) | This topic for the IT professional answers frequently asked questions concerning the requirements to use, upgrade, deploy and administer, and key management policies for BitLocker. |
| Prepare your organization for BitLocker: Planning and policies | This topic for the IT professional explains how can you plan your BitLocker deployment. |
| BitLocker basic deployment | This topic for the IT professional explains how BitLocker features can be used to protect your data through drive encryption. |
| BitLocker: How to deploy on Windows Server | This topic for the IT professional explains how to deploy BitLocker on Windows Server. |
| BitLocker: How to enable Network Unlock | This topic for the IT professional describes how BitLocker Network Unlock works and how to configure it. |
| BitLocker: Use BitLocker Drive Encryption Tools to manage BitLocker | This topic for the IT professional describes how to use tools to manage BitLocker. |
| BitLocker: Use BitLocker Recovery Password Viewer | This topic for the IT professional describes how to use the BitLocker Recovery Password Viewer. |
| BitLocker Group Policy settings | This topic for IT professionals describes the function, location, and effect of each Group Policy setting that is used to manage BitLocker. |
| BCD settings and BitLocker | This topic for IT professionals describes the BCD settings that are used by BitLocker. |
| BitLocker Recovery Guide | This topic for IT professionals describes how to recover BitLocker keys from AD DS. |
| Protect BitLocker from pre-boot attacks | This detailed guide will help you understand the circumstances under which the use of pre-boot authentication is recommended for devices running Windows 10, Windows 8.1, Windows 8, or Windows 7; and when it can be safely omitted from a device’s configuration. |
| Protecting cluster shared volumes and storage area networks with BitLocker | This topic for IT pros describes how to protect CSVs and SANs with BitLocker. |
| Enabling Secure Boot and BitLocker Device Encryption on Windows 10 IoT Core | This topic covers how to use BitLocker with Windows 10 IoT Core |
BitLocker’s full-disk encryption normally requires a computer with a Trusted Platform Module (TPM). Try to enable BitLocker on a PC without a TPM, and you’ll be told your administrator must set a system policy option.
BitLocker is available only on Professional, Enterprise, and Education editions of Windows. It’s also included with Windows 7 Ultimate, but isn’t available on any Home editions of Windows.
Why Does BitLocker Require a TPM?
RELATED:What is a TPM, and Why Does Windows Need One For Disk Encryption?
BitLocker normally requires a Trusted Platform Module, or TPM, on your computer’s motherboard. This chip generates and stores the actual encryption keys. It can automatically unlock your PC’s drive when it boots so you can sign in just by typing your Windows login password. It’s simple, but the TPM is doing the hard work under the hood.
Quote: ================================================ MCU Version: V 07.30 07-05-09 RM-237 (c) Nokia. IMEI Plain: 27016 IMEI Spare: A27010 IMEI SV: 0270127F Phone Model: Nokia 3110c Category: Classic Phone Phone Type: RM-237 ================================================ Extended Phone Information ================================================ Product Code: 0544311 PPM SW Version: V 07.21 05-11-08 RM-237 (c) Nokia. > > > > Nokia 3110c phone restricted User Name Remember Me? Nokia 3110c v 07.30 rm 237 software.
If someone tampers with the PC or removes the drive from the computer and attempts to decrypt it, it can’t be accessed without the key stored in the TPM. The TPM won’t work if it’s moved to another PC’s motherboard, either.
You can buy and add a TPM chip to some motherboards, but if your motherboard (or laptop) doesn’t support doing so, you may want to use BitLocker without a TPM. It’s less secure, but better than nothing.
How to Use BitLocker Without a TPM
You can bypass this limitation through a Group Policy change. If your PC is joined to a business or school domain, you can’t change the Group Policy setting yourself. Group policy is configured centrally by your network administrator.
If you’re just doing this on your own PC and it isn’t joined to a domain, you can use the Local Group Policy Editor to change the setting for your own PC.
To open the Local Group Policy Editor, press Windows+R on your keyboard, type “gpedit.msc” into the Run dialog box, and press Enter.
Navigate to Local Computer Policy > Computer Configuration > Administrative Templates > Windows Components > BitLocker Drive Encryption > Operating System Drives in the left pane.
Double-click the “Require additional authentication at startup” option in the right pane.
Select “Enabled” at the top of the window, and ensure the “Allow BitLocker without a compatible TPM (requires a password or a startup key on a USB flash drive)” checkbox is enabled here.
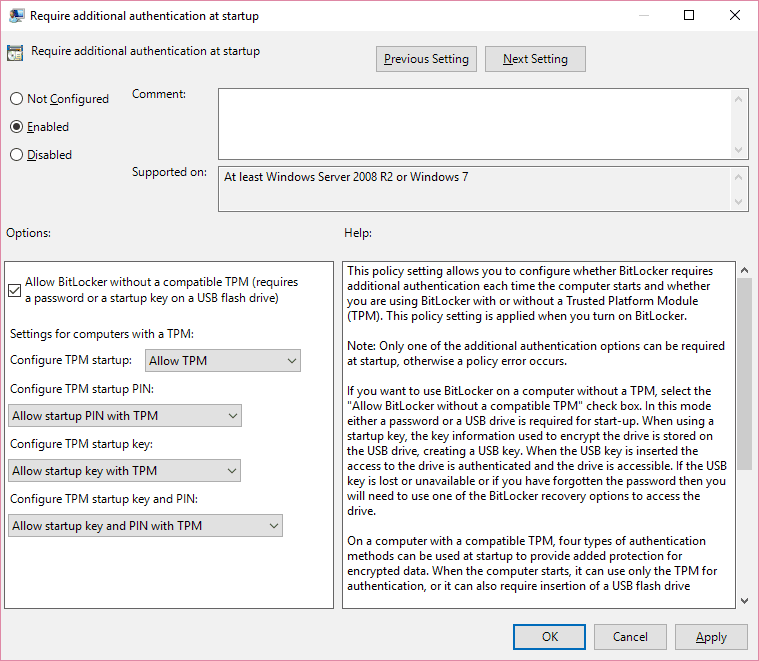
Click “OK” to save your changes. You can now close the Group Policy Editor window. Your change takes effect immediately—you don’t even need to reboot.
How to Set Up BitLocker
You can now enable, configure, and use BitLocker normally. Head to Control Panel > System and Security > BitLocker Drive Encryption and click “Turn on BitLocker” to enable it for a drive.
You’ll first be asked how you want to unlock your drive when your PC boots up. If your PC had a TPM, you could have the computer automatically unlock the drive or use a short PIN that requires the TPM present.
Because you don’t have a TPM, you must choose to either enter a password each time your PC boots, or provide a USB flash drive. If you provide a USB flash drive here, you’ll need that flash drive connected to your PC each time you boot up your PC to access the files.
RELATED:How to Set Up BitLocker Encryption on Windows
Continue through the BitLocker setup process to enable BitLocker drive encryption, save a recovery key, and encrypt your drive. The rest of the process is the same as the normal BitLocker setup process.
When your PC boots, you’ll have to either enter the password or insert the USB flash drive you provided. If you can’t provide the password or USB drive, BitLocker won’t be able to decrypt your drive and you won’t be able to boot into your Windows system and access your files.
READ NEXTBitlocker Windows 10 Not Showing Up
- › How to Enable Google Chrome’s New Extensions Menu
- › How to Stop Spammers From Attacking Your Google Calendar
- › How to Power Off Your Samsung Galaxy Note 10 or 10 Plus
- › How to Switch from a Windows PC to a Mac
- › Want to Survive Ransomware? Here’s How to Protect Your PC